These are being setup to be used with tryhackme and hack the box, both of which are great platforms to work on your skills in cybersecurity. While you can use any distro of your liking and just install the necessary security tools, there are several distros already pre-packaged with the most commonly used tools. The two of which will be used here are ParrotOS and Kali Linux.
Local Setup With Virtual Machine
For the local vm, I will be using VMware and the OS will be ParrotOS, but kali does have pre-built VM’s for virtualbox, vmware, hyper-v and qemu, that makes the setup process easier.
After downloading your choice of OS and Virtualization platform, you’ll create a new virtual machine and follow along the wizard to get the machine up and running.
You’ll then start the machine and either use it as a live instance of the OS or start the installation process of the OS on that machine. You may need to click on enter fullscreen mode to avoid screensize issues as well as changing the resolution in the display settings.
Click on the Install Parrot icon on the desktop and follow along the installer.

After the installation is finished, we can change the resolution to fix any of the issues.

And lastly, we can open up firefox and head over to tryhackme or hack the box and download the openvpn profile we’ll use to connect to their services when going through their programs. For tryhackme, it can be found by logging in, clicking your profile and clicking access.
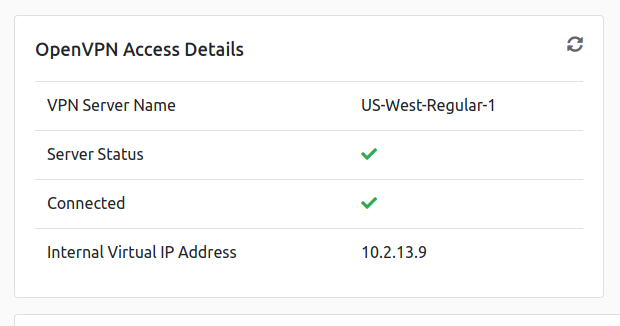
Once downloaded, open up a terminal and cd into the directory you saved the ovpn file. From there simply run openvpn {username}.ovpn and go back to tryhackme and refresh to see that you are now connected.
And that’s it for the local vm, from there you can start messing around with any of the tools and get familiar with the command line and work on the labs.
Server docker setup
Firstly, you’ll need to get a server, whether it’s from hetzner, linode, gcp, aws, azure or your favorite cloud provider.
Next you’ll want to update the machine, debian based (e.g. Ubuntu) sudo apt update && sudo apt upgrade -y.
From there, you want to install Docker and Docker Compose.
curl -sSL https://get.docker.com/ | CHANNEL=stable sh
curl -L "https://github.com/docker/compose/releases/download/$(curl -s https://api.github.com/repos/docker/compose/releases/latest | grep "tag_name" | cut -d\" -f4)/docker-compose-$(uname -s)-$(uname -m)" -o /usr/bin/docker-compose \
&& chmod +x /usr/bin/docker-compose \
&& docker-compose version
Once again, both Kali and Parrot have docker images to be able to be used on any system that docker is available on. Kali linux Docker and Parrot on Docker.
Parrot
The following command gives a docker container for Parrot that will be removed on exit, as well as give access to a volume in the current directory to be used to share files with the host.
$ docker run --rm -ti --network host -v $PWD/work:/work parrot.run/security
you can remove the
--rmif you’d like to keep the container once exited.
Once connected you can update and install any other tools you may need.
$ apt update && apt install {package} -y
Kali Linux
The following commands will download and run a docker container for Kali and allow the use of it on the server.
$ docker pull docker.io/kalilinux/kali-rolling
$ docker run --tty --interactive --sysctl net.ipv6.conf.all.disable_ipv6=0 --cap-add=NET_ADMIN -v $PWD/work:/work kalilinux/kali-rolling
And once in the docker for kali, running the following command to download and install all the necessary tools. This process will take a while.
$ apt update && apt -y install kali-linux-headless
These are cli only* and a more hands on approach, but they allow for a hacking setup that you can access from anywhere as long as you can get an ssh client. Using them to work with tryhackme and hack the box will require downloading the openvpn configuration file from the respective site, using SFTP or SCP to upload it to the server and move it into the $PWD/work folder to be used in the docker container.
From there, I would recommend using a tool like tmux or an alternative such as zellij to run the openvpn command in the docker container and then pressing ctrl+b & d to detach from the tmux session and go back to use the tools to work on your Labs/CTFs.
Closing
And with all that, you now have a hacking setup to be put to use on CTFs, labs, for learning more about linux, personal security checks on any infastructure you may have, or just for the experience in setting it up.
*There are ways to get desktop versions accessable through the browser using kasm, but that may be for another time.